VPN vs. Proxy vs. Tor: Which One to Choose for Online Anonymity
VPNs and proxies both promise to hide your IP address and provide protection, but they do so in completely different ways.
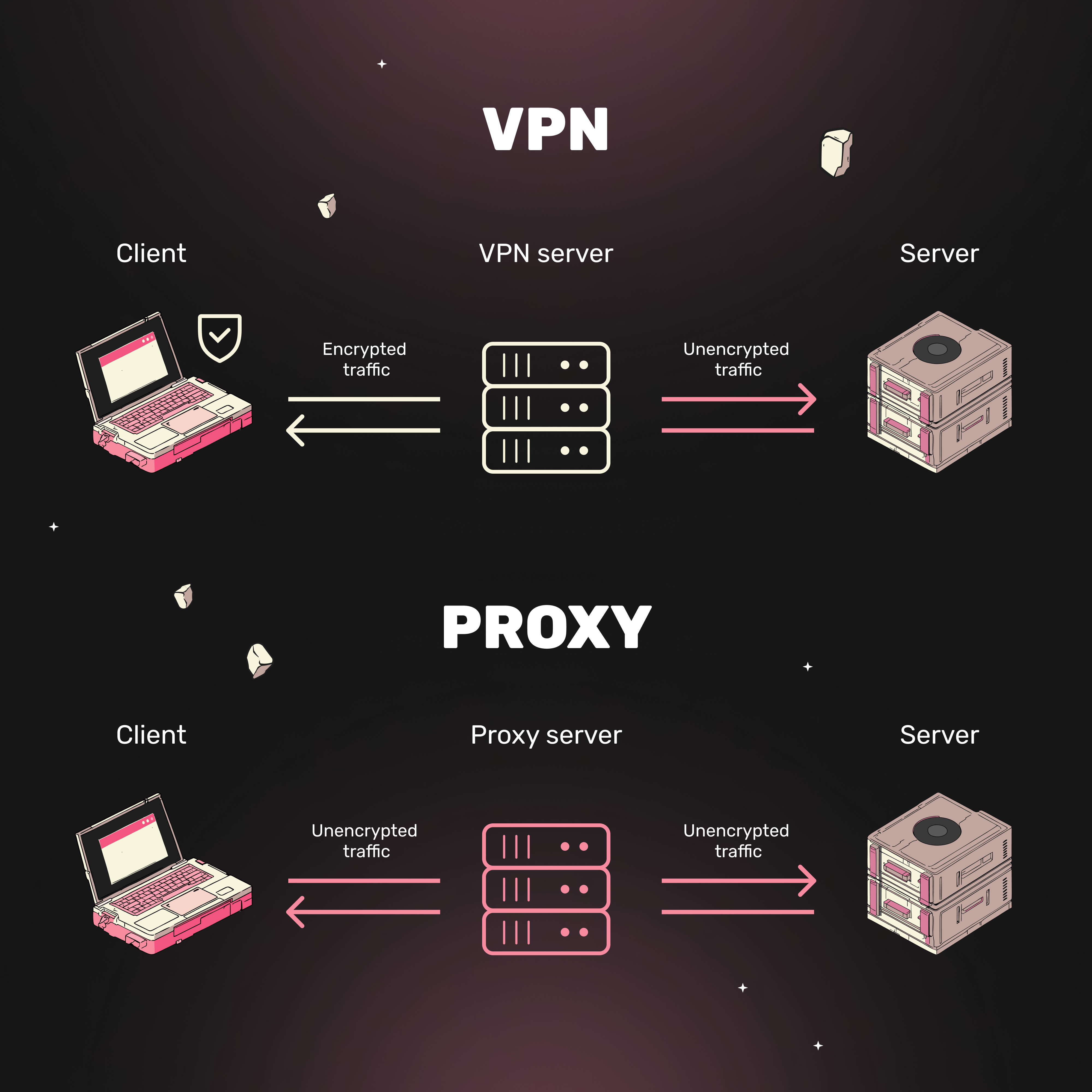
A VPN is like a reliable bodyguard, surrounding you with invisible protection. All your data is encrypted, your routes are hidden, and tracking your actions becomes nearly impossible.
Imagine this: You connect to a public Wi-Fi network in a café. The VPN instantly secures your connection with a protected channel—a so-called "VPN tunnel." Even if someone tries to intercept your data, all they’ll see is "encrypted garbage."
A proxy, on the other hand, acts as an intermediary. Like a VPN, it takes your request and forwards it, masking your real IP. However, a proxy does not encrypt data.
If you need complete data protection, a VPN is the clear choice—especially a decentralized VPN like KelVPN, which offers quantum-level security and maximum anonymity due to its unique architecture, making it technically impossible to collect personal data.
For simpler tasks—like bypassing geo-restrictions—a proxy might suffice. But if you want to protect your passwords, banking details, or private correspondence, you need something smarter.
What Is a VPN?
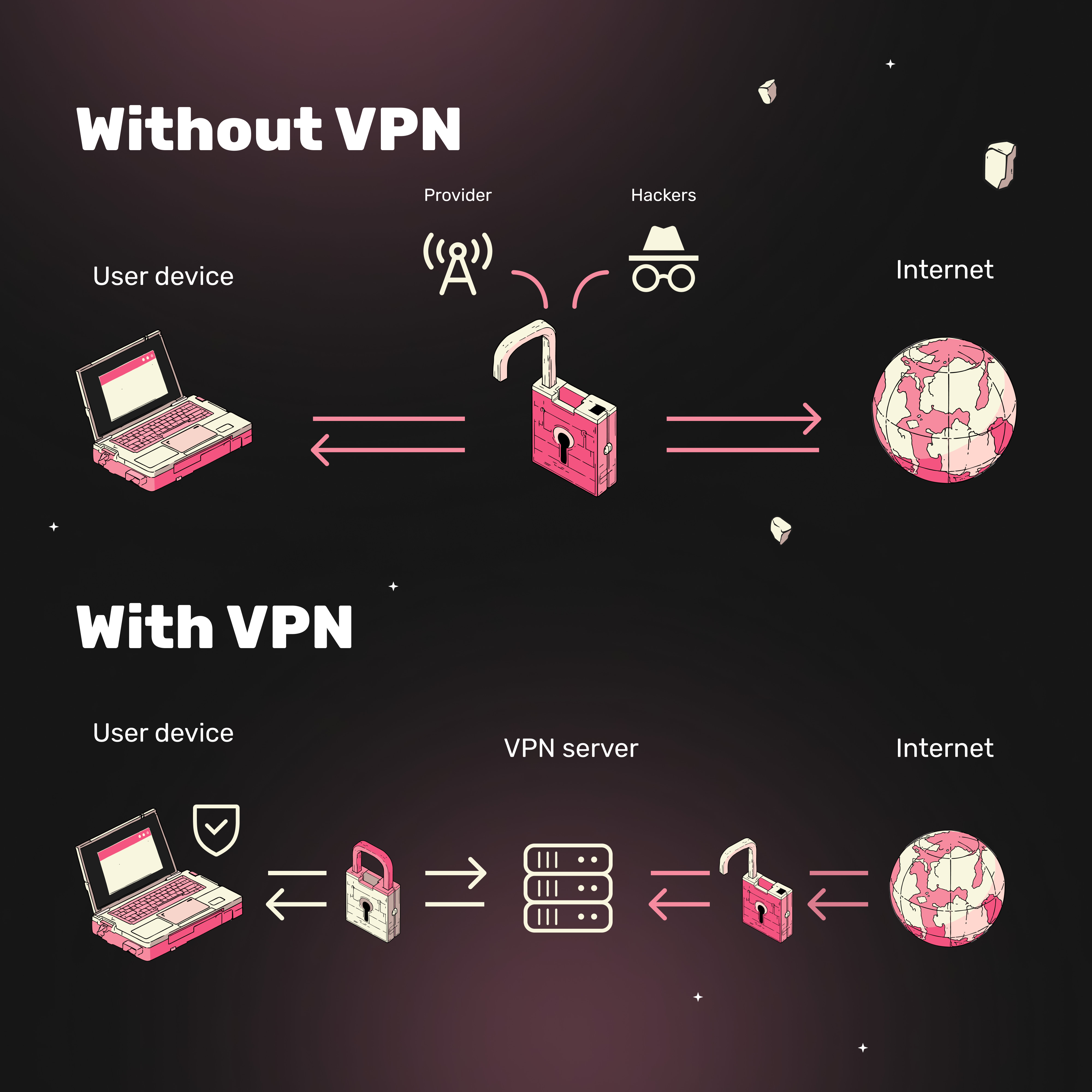
Imagine this: You visit a website, check your email, or connect to public Wi-Fi at a café. Now pause for a second and think—your data could end up not just with your ISP but also in the hands of hackers.
A VPN is your personal shield on the internet, protecting your data and masking your IP. No ISP or malicious actor can peek into the secure tunnel created between your device and the VPN server. Your IP address stays hidden, and your activity remains private.
Types of VPNs
Free VPNs
Accessible but limited. Suitable for temporary use (e.g., bypassing geo-blocks). But remember: If the service is free, you might be paying with your data.
Paid VPNs
A more serious approach—higher speeds, global server coverage, no ads, and guaranteed privacy. Ideal for long-term use, especially for securing financial and personal data.
Example: You pay for a subscription and gain confidence that no one else knows which sites you visit.
Decentralized VPNs
Built on blockchain, these VPNs have no central servers or single points of control, minimizing risks.
Unlike traditional VPN providers with scattered servers, a decentralized VPN is a distributed network of independent nodes operating on blockchain principles. This not only expands coverage but also eliminates centralized control—you connect to a dynamic network of peers, not a corporate server. This improves reliability (e.g., if nodes fail) and ensures anonymity since data cannot be centrally tracked or collected.
Quantum-Resistant VPNs
Welcome to the future of security. These VPNs use algorithms that protect data even from quantum computer hacking.
Example: KelVPN, a quantum-secure decentralized network, offers cutting-edge solutions for peace of mind.
What Is a Proxy?
A proxy is an intermediary between your device and the internet. When you send a request, the proxy intercepts it, processes it, forwards it to the target website, and then returns the response—hiding your real IP. Simple in concept, but this comes with both functionality and limitations.
How Does a Proxy Work?
- You send a request (e.g., visiting a site, streaming video, opening an app).
- Your device connects to the proxy first.
- The proxy forwards the request to the target website under its own IP.
- The website sends data back to the proxy.
- The proxy delivers the response to you.
Proxy vs. VPN: Key Differences
Animation: How VPN Works
Your Device
VPN Client
Encrypted
ISP
Encrypted
VPN Server
Internet
Device
VPN
Encrypted
ISP
Encrypted
VPN
Web
Animation: How Proxy Works
Your device
Proxy client
Unencrypted traffic
ISP
Unencrypted traffic
Proxy server
Website
Device
Proxy
No encryption
ISP
No encryption
Proxy
Website
Data Encryption: Proxy Loses to VPN
A VPN encrypts all traffic, making it unreadable to ISPs or hackers. A proxy does not encrypt data—your credit card details, for example, remain exposed.
Performance: Speed vs. Security
A VPN may slightly slow your connection due to encryption but offers stability. Free proxies often suffer from overload and low speeds (their infrastructure is usually minimal).
Cost: Free Isn’t Always Better
Many proxies are free but may log/sell your data or misuse your traffic. Most VPNs are paid, ensuring reliability, privacy, and quality.
Coverage: Traffic Scope
A VPN protects all device connections (apps, browsers, etc.). A proxy only works per application (e.g., one browser), limiting its use.
Privacy: Who Keeps Logs?
Most VPNs enforce a strict no-logs policy, leaving no trace of your activity. Proxies (especially free ones) rarely guarantee this, making them a trade-off between convenience and anonymity.
Types of Proxy Servers
Proxy servers provide diverse capabilities for routing internet traffic. Different types are suited for different purposes, ranging from simple anonymity to complex business tasks.
HTTP Proxies
These proxies work exclusively with web traffic. By configuring your browser, an HTTP proxy redirects requests through a remote server, hiding your IP address. They are particularly popular among users who need to bypass geographical restrictions, for example, to watch videos available only in specific regions. However, caution is advised: HTTP proxies do not encrypt transmitted data. This makes them vulnerable when performing tasks requiring confidentiality, such as online banking. Using websites with SSL certificates is mandatory in such cases.
SOCKS5 Proxies
These proxies go beyond web browsers, supporting applications for file sharing, video streaming, and even online games. They provide more flexible traffic redirection than HTTP proxies. Nevertheless, free SOCKS5 proxies often suffer from low speeds. The reason is simple: limited infrastructure leads to slow performance under high loads.
Transparent Proxies
Such proxy servers are most commonly used for content control and filtering. For instance, schools, companies, and libraries implement them to block unwanted websites. Interestingly, users may not even be aware of a transparent proxy's presence, as it requires no additional device configuration. This makes them an effective tool for organizations seeking to restrict access to certain resources.
The History of Proxies
The idea of proxy servers originated in the 1990s, when the internet was just beginning to develop actively. Initially, they were created to speed up page loading and reduce server load through data caching.
Over time, their functionality expanded significantly. By the late 20th century, proxies began to be used for anonymization, content filtering, and network protection. Today, they hold an important place in internet infrastructure, offering broad capabilities for users worldwide.
Why Are Proxies Often Free?
The phrase "free proxy" sounds appealing, but what lies behind it?
- Advertising model: Companies often provide proxy services for free in exchange for displaying ads. This helps cover server and maintenance costs.
- Public initiatives: Nonprofit organizations or enthusiasts create free proxies to make the internet accessible to everyone.
However, don’t overlook premium proxies. They offer:
- High speeds even under heavy loads.
- Enhanced security, including DDoS protection.
- A wide range of server locations.
For casual browsing, a free option may suffice, but for tasks involving privacy or professional needs, a paid service is preferable.
Each proxy type has its strengths and weaknesses. The choice between free and paid depends on your priorities—speed, privacy, or ease of use.
Tor
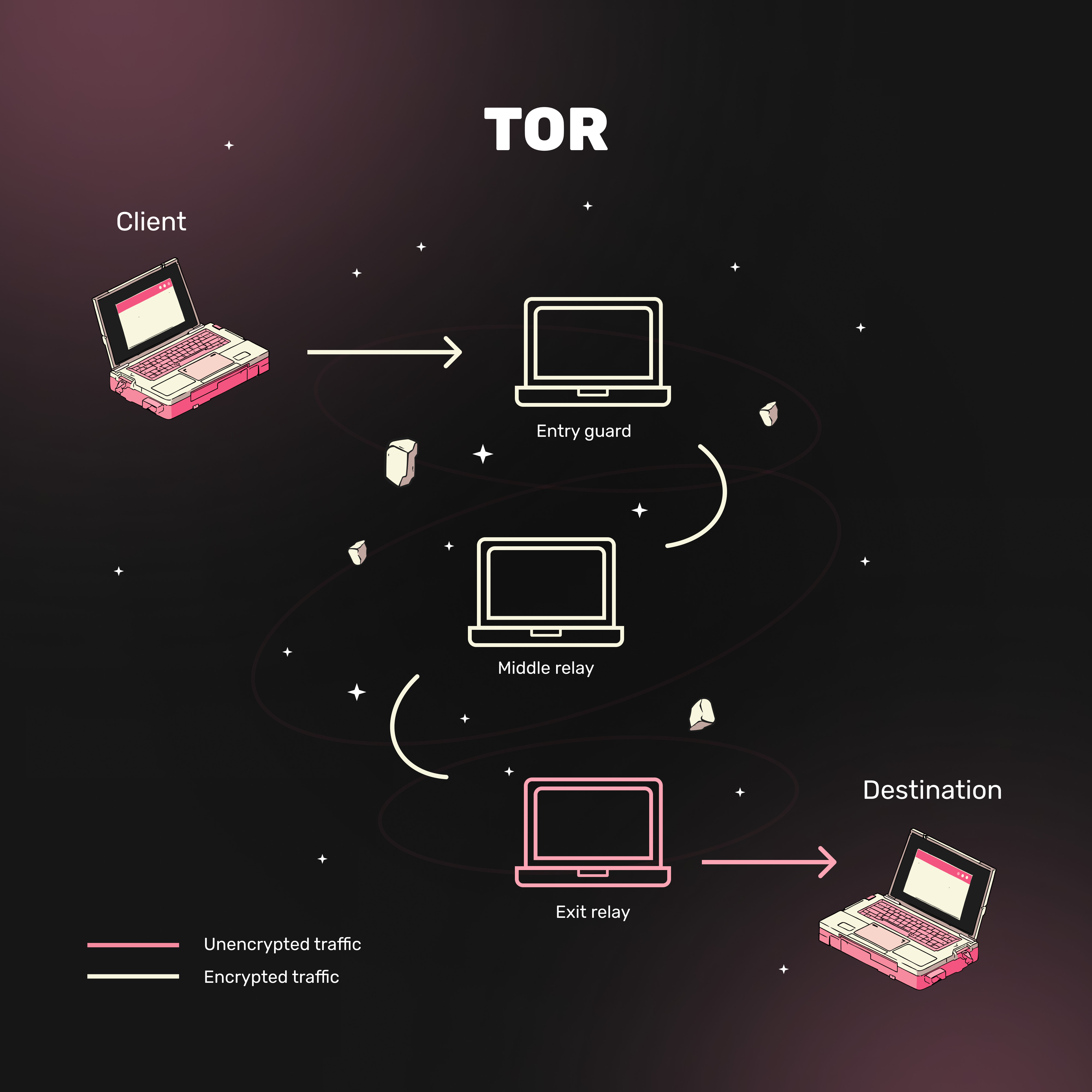
Tor, short for The Onion Router, is one of the most sophisticated tools for ensuring online anonymity. But how secure is it really?
Tor is an anonymous network built on a chain of proxy servers that create encrypted virtual tunnels. Unlike regular proxies or VPNs, Tor uses onion routing: data (the "core") is sequentially encrypted in multiple layers (like an onion's skins) and transmitted through three random network nodes. Each node reveals only one encryption layer, learning just the address of the next link in the chain—not the original request or final recipient. This eliminates the possibility of traffic tracking, even if individual nodes are compromised.
User traffic passes through three key servers (nodes):
- Entry Node
- Middle Node
- Exit Node
This process is necessary to hide the IP address. Each node knows only the address of the previous one in the chain, making it impossible to trace the original IP by the time the user exits the network.
Your traffic is protected by three layers of encryption. The first two nodes see only encrypted layers, while the exit node decrypts the final request to the internet. These nodes are operated by network users on their devices—the more participants, the more secure and efficient the network becomes.
Access to the Tor network is provided through the Tor Browser, based on a modified version of Firefox ESR. According to its developers, the browser can block unwanted tracking, preventing personal data collection and forcing sites to use encryption. However, in practice, this tool is not without flaws.
Using Tor may draw attention from law enforcement, as its usage is easily detectable. For added security, combining Tor with a VPN is recommended.
Operators of exit nodes bear responsibility for users’ actions and can monitor traffic, potentially identifying users. This makes them a target for law enforcement.
Due to multi-layered encryption, the Tor network is slow, and many websites may not function properly through the Tor Browser.
Understanding the differences between VPNs, proxies, and Tor is essential for making informed decisions about online security and privacy.
VPNs offer comprehensive encryption, broad coverage, and superior privacy policies, making them ideal for protecting online activities.
Proxies, while useful in specific contexts, do not provide the same level of security and are often slower.
Tor delivers maximum anonymity but comes with speed trade-offs and complexity.
Your choice should depend on your specific needs and the level of security you require.
Proxy, VPN, KelVPN
When choosing between VPN, proxy, decentralized VPN, and KelVPN, it's important to consider diverse needs and usage scenarios.
VPN has become something of a standard for protecting online activities, offering a high level of security and privacy. It's ideal for bypassing geo-restrictions, securing connections on public networks, and protecting data in remote work environments.
The cost of VPN services typically reflects their high functionality and reliability. Proxies, on the other hand, are often used for more specific tasks like bypassing website blocks or network access control. They can also be a more budget-friendly option, especially when choosing free services. However, proxies may be less secure compared to VPNs, particularly regarding DNS leak protection.
With decentralized VPNs in general and quantum-secure KelVPN in particular, new possibilities emerge for ensuring online anonymity and security. Decentralized VPNs offer distributed server networks, making them more resistant to blocking and valuable for data protection. KelVPN, using quantum cryptography, promises revolutionary changes in online security, offering unparalleled protection levels.
Ultimately, the choice between these tools depends on your specific needs, budget, and desired level of online protection. A wise decision can be made by carefully analyzing the information presented and considering your personal priorities regarding online security and anonymity.
FAQ
There are several reasons why you might want to use VPN or proxy:
| Feature | VPN | Proxy |
|---|---|---|
| Security | Protects your data from cyber threats and ensures high privacy | Hides your IP address, useful for accessing restricted content |
| Content Access | Allows bypassing geo-restrictions for all online services | Provides access to geo-blocked sites through specific applications |
| Privacy | Protects all your internet activities | Only hides IP for specific apps or browsers |
VPNs are becoming increasingly popular due to their high security and convenience.
Firewall controls incoming/outgoing traffic and blocks unwanted connections at OS/network level, compatible with VPN/Tor
VPN encrypts all device internet traffic and masks IP address (can be used before/after Tor, affecting anonymity levels)
Tor routes traffic through node chains, hiding data sources
Speed reduction due to data encryption and remote server routing
Cost - quality VPN services are often paid (free options may be less reliable)
Compatibility - not all devices/platforms support VPN
Legal restrictions - some countries prohibit or limit VPN use
Purpose: VPN better for privacy/security, proxy for geo-unblocking and speed
Security: VPN offers higher encryption and data protection
Speed: proxies typically faster as they encrypt only part of traffic
Compatibility: ensure service supports your devices/OS
Cost: compare pricing for different services
Setup complexity: some require advanced configuration
Speed/stability: proxies may be unstable, causing interruptions
Security: no data encryption (less secure than VPN)
Service quality: free proxies often overloaded
Security: encrypts traffic, ensuring privacy
Stability: reliable VPNs provide uninterrupted connections
Content access: unlocks region-locked content worldwide