What is VPN?
What is a VPN and how does it work?
A VPN (Virtual Private Network) is a tool that, uses a special encryption algorithm and a function to connect you to a remote server. This hides your IP address, replacing it with a new one and thus ensuring the security and confidentiality of your internet connection.
- Secure connection
- IP address masking
- Access to any content
What is a VPN?
A VPN (Virtual Private Network) is a technology that, like a protective veil, envelops your internet connection, encrypting it and hiding your real IP address. This ensures the privacy and security of your online presence, allowing you to freely and anonymously explore the vast expanses of the Internet.
VPN Usage Legality Notice
VPN services are intended to ensure the security, privacy, and protection of users' data online. We strongly recommend using the VPN service in accordance with the laws of your country. Using a VPN to bypass copyright restrictions, censorship, or other legal limitations may violate the laws of your country or the policies of certain services. Users are fully responsible for complying with local laws and regulations when using the VPN service. All information on this website is provided for informational purposes only and is not intended to encourage legal violations.
VPNs are used for:
- Protecting privacy on the Internet. This is especially true if your VPN service is based on a decentralized model. Such VPNs do not allow for the storage and collection of user data in one place.
- Preventing surveillance and discrimination based on location, thanks to special VPN servers.
- Accessing corporate networks when an IP address of a specific country is required.
- Bypassing geographical restrictions and accessing any online content worldwide.
- Protection from cyberattacks.
A Virtual Private Network, or VPN, acts as a secure corridor for your internet traffic. This is particularly valuable when using public Wi-Fi networks where your data is most vulnerable. Instead of traveling openly on the information highways, a VPN creates an isolated channel for you, connecting to a remote server and masking your real IP address. Encryption add another layer of anonymity by turning your data into unreadable code. All this together allows you to securely hide your digital identity in the online space.
Different VPN services vary in their encryption methods and approaches to server infrastructure organization. For example, in a decentralized VPN, each user can become part of the network, providing their channel for data transmission and receiving rewards in the form of tokens. In the classic variant, all servers belong to one company, which can pose risks of personal data collection.
How a regular VPN works
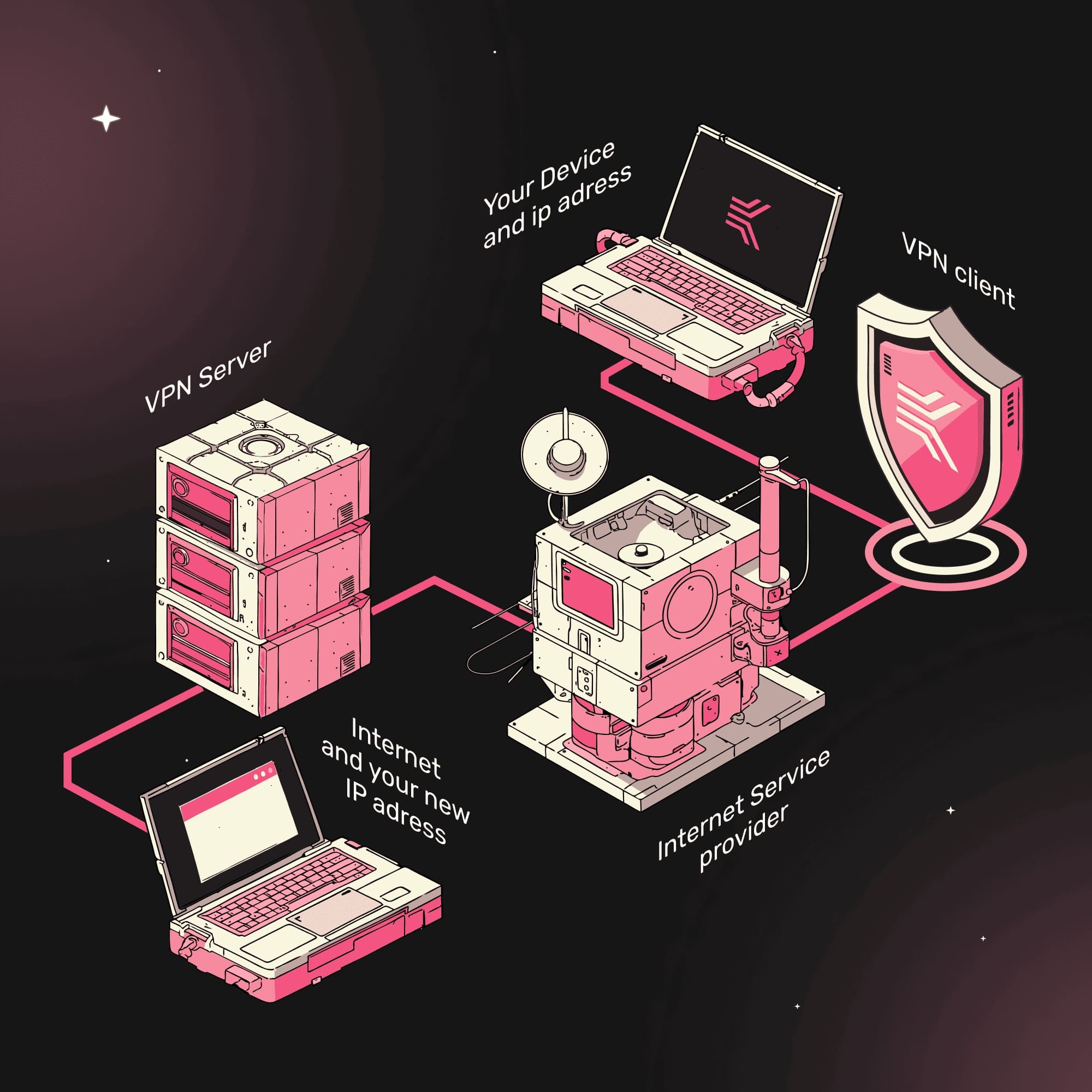
Unlike a direct path where your internet traffic goes through the provider's servers, a VPN offers an alternative route, directing data through a dedicated server and encrypting it all the way. This allows you to hide your true IP address, securely protecting your digital identity. Thanks to this, you can freely navigate the Internet and bypass any access restrictions without fearing for the confidentiality of your data.
What is an IP Address?
Imagine the vast expanse of space filled with countless stars, each shining with its unique light. Every star has its coordinates that allow us to determine its position in this boundless space. Similarly, every computer or device connected to the Internet has its unique identifier – an IP address.
An IP address acts as a kind of digital passport consisting of a sequence of numbers that allows devices on the network to find each other and establish a connection. It serves as both an identifier and a navigator for data, similar to a postal address that ensures the delivery of a letter to its destination.
- Uniqueness: Just as each star occupies its unique place in space, each IP address is unique within its network. This allows devices to accurately identify each other, like spacecraft navigating by star maps.
- Diversity: In the world of IP addresses, there is diversity, just like in the world of stars, where celestial bodies differ in size and color. For example, static IP addresses remain unchanged, like fixed stars, while dynamic IP addresses can change, resembling the movement of comets.
- Visibility: Like stars visible from Earth, IP addresses are accessible for observation by other devices on the network. This allows various services to track your location and activity, much like astronomers study the movements of celestial bodies.
Understanding the principles of IP addresses opens the door to understanding how the Internet works and helps us appreciate the importance of protecting privacy online. Just like observing the stars, it is important to remember the scale and complexity of the digital universe, where each address is a unique beacon.
It is worth noting that IP addresses are not always static; they can be dynamic and change over time. When using a VPN, your IP address can transform into any other, creating an additional layer of anonymity.
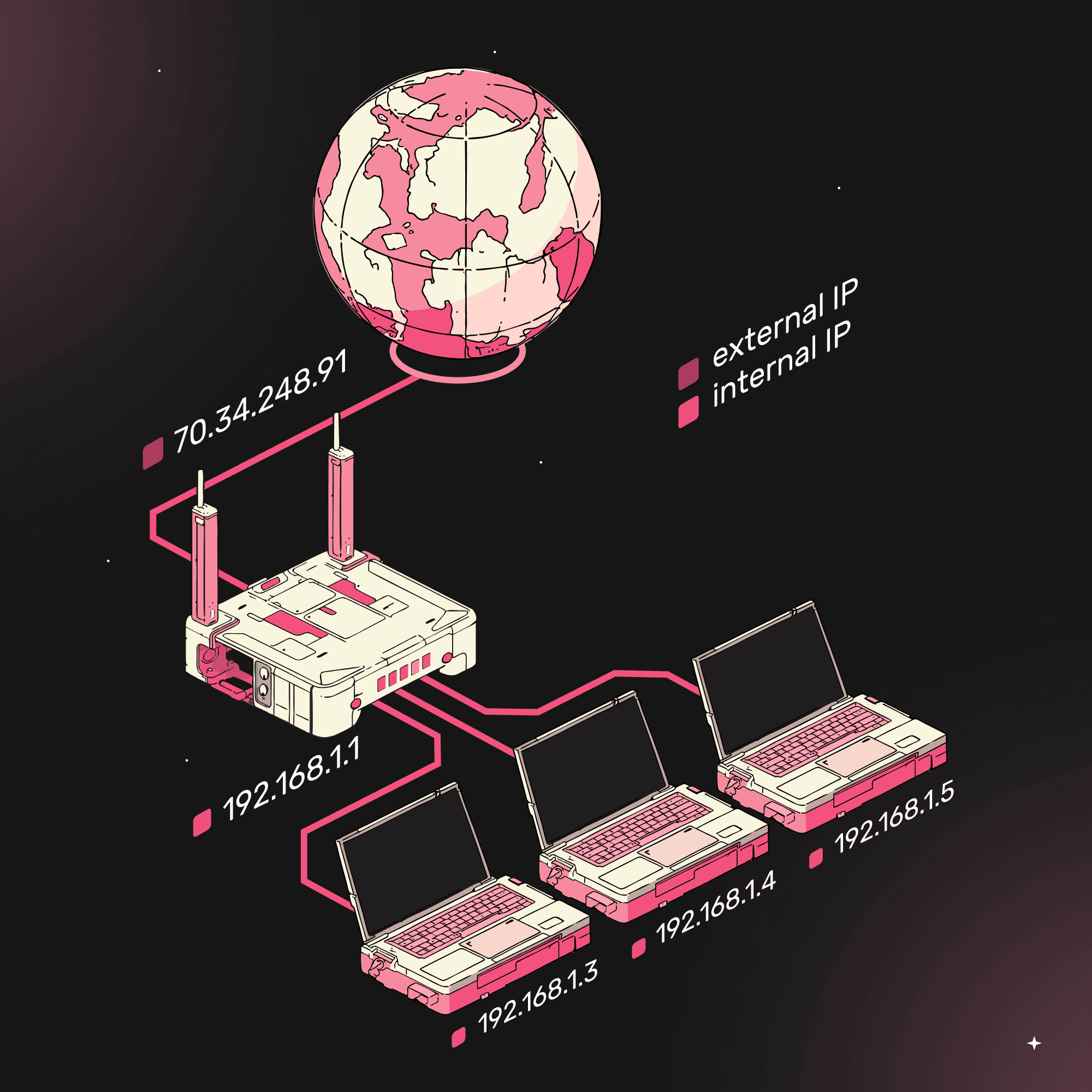
Structure of an IP Address:
An IP address version 4 (IPv4), the most common format of a digital address, is a combination of four numbers separated by dots, for example, 192.168.1.1. Each number can range from 0 to 255, allowing for over 4 billion unique addresses. However, not all IP addresses are equal, and there are two main types: internal and external.
An internal IP Address is assigned to a device within a local network, such as a home or office. It allows devices within this network to interact with each other, like when, a computer send documents to a printer.
External IP Address is assigned to your local network by your Internet Service Provider. It serves to identify your network in the global internet space and allows devices within the local network to communicate with the external world.
Quantum-Secured VPN
Traditional VPNs, while effective against current cyber threats, may be vulnerable to future attacks from quantum computers. To address this emerging issue, quantum-secured VPNs offer a reliable solution using advanced cryptographic algorithms.
For example, a VPN service like KelVPN provides quantum-secured encryption that ensures the reliable protection of your Internet connection.
According to NIST forecasts, the CRYSTALS-Dilithium algorithm and Kyber 512 protocol will become the standard in five years. But they can already protect your data from cyber threats today, including attacks from quantum computers.
Decentralized VPN

A decentralized VPN is an application that connects two or more networks via the Internet. This type of virtual private network does not rely on a centralized server for routing internet traffic like a classic VPN. Instead, it distributes connections through a network of nodes managed by individual users.
A regular VPN is like a large river flowing along a predetermined path. It is fast and efficient, but you depend on a central authority (such as a government or company) that controls the flow of water and may charge for using this river.
A decentralized VPN is like a network of small rivers, lakes, and streams interconnected with each other. Like water, VPN traffic flows freely along different paths independently of any central authority. This ensures greater flexibility and resilience to failures.
Learn more about decentralized VPN.
Classic VPN, Decentralized, or Quantum-Secured?
Regular VPN
- Privacy Protection : Encrypts the internet connection, hiding the IP address and protecting data from interception.
- Prevents Tracking and Discrimination Based on Location : Hides the real location, preventing tracking and location-based discrimination.
- Protection from Cyberattacks : Secures the network connection, preventing data interception and cyberattacks.
Decentralized VPN
- Privacy Protection : Distributes connections through a network of nodes, not relying on a central server. This increases privacy and resistance to censorship.
- Prevents Tracking and Discrimination Based on Location : Provides an even higher level of privacy as network nodes cannot track user activity.
- Protection from Cyber Attacks : Offers increased resilience to cyberattacks by using distributed nodes that have no single point of failure.
How Does Protection Work and What Does a VPN Hide?
A VPN hides your IP address and encrypts your traffic, but it VPN does not mask your operating system.
Your IP address is a unique identifier for your device on the network., The address can be used to track your activity and determine your location. VPN encryption makes your traffic unreadable, making it difficult to track your actions on the Internet.
However, the operating system managing your computer or mobile device remains visible on the websites and services you visit. This is because the operating system is not part of the internet traffic; it functions on your device and is not transmitted through the VPN connection.
A VPN is a powerful tool for ensuring security, but it is not a guarantee of anonymity. Choosing a reliable VPN provider and following cybersecurity practices is key to protecting your data and privacy.
Masking Traffic and Location
A VPN routes your internet traffic through remote servers, as if through secret tunnels. Your IP address and physical location become invisible to websites and prying eyes. When accessing a site through a VPN, the source of your connection appears as one of the many VPN routers, not your device.
VPN provides a high level of anonymity but not absolute invisibility. VPN brings you closer to true anonymity but does not reach the level of the Tor network*, which uses volunteer relays to disperse your connection.
*Compared to Tor, a VPN provides higher data transfer speeds, making it a more preferred option for most users. More about VPN vs. Proxy vs. Tor.
Risks and Limitations of VPN
 1. Data Leaks: Free or unreliable VPNs may share information with third parties, leading to leaks of IP addresses, DNS requests, or WebRTC connections. To avoid this issue, it is recommended to use a VPN service with a good reputation. |  2. Insecure Protocols: The PPTP (Point-to-Point Tunneling Protocol) is considered outdated and vulnerable. It is recommended to prefer more secure options. |  3. Lack of Anonymous Payments: Some VPN providers do not offer anonymous payment options, which can reduce privacy. When choosing a VPN, look for payment options using cryptocurrency or anonymous payment systems. |
 4. Malicious Threats: Poor quality VPN services may be compromised by malware, which can track your activity. It is important to choose thoroughly vetted and reliable VPN providers. |  5. Limitations of Free Solutions: Free VPN services often have limitations on speed, number of available servers, and data transfer volume. To ensure data stability and security, consider options with a paid subscription. |  6. Government Regulation: In some countries, the use of VPNs may be restricted or even banned. Before using a VPN, it is wise to familiarize yourself with the laws of your country. |
History of VPN
Originally, VPN technology was conceived as a tool to provide access to networks belonging to corporations, universities, schools, and government organizations. The main idea was to allow remote employees to access the resources of these organizations through a secure connection.
1960s
The U.S. Department of Defense was actively involved in projects aimed at encrypting online communications. The result of these projects was ARPANET, a packet-switching network that laid the foundation for creating the TCP (Transfer Control Protocol) and IP (Internet Protocol) protocols.
1993
A team of specialists from Columbia University and Bell Labs developed the first version of the modern VPN called swIPe. This was an important step toward creating accessible and effective tools for securing online connections.
1996
Microsoft employee Gurdeep Singh-Pall developed the Point-to-Point Tunneling Protocol (PPTP), which allowed users to securely connect to remote networks. PPTP became one of the first widely used VPN protocols.
Today
VPNs are available to any user interested in ensuring privacy and security while working on the Internet. VPN services help protect personal data, hide IP addresses, and ensure the anonymity of online activities.
Double VPN (Multi-Hop): Double Protection for Your Online Activity
Double VPN (Multi-Hop) is an innovative feature of Virtual Private Networks (VPN) that provides an additional layer of security and privacy. Let's break down how it works and the advantages this technology offers.
Double VPN (Multi-Hop)
A regular VPN creates a secure tunnel between your device and a VPN server, hiding your IP address and securing data transmission.
Double VPN adds another layer of protection by routing your traffic through two VPN servers, forming a sequential or cascading VPN connection. This means data is encrypted twice, significantly increasing privacy and security.
Multi-Hop VPN, synonymous with Double VPN, allows multiple VPN connections simultaneously but may slightly (and sometimes significantly) reduce device speed.
Why Use Double VPN?
Double VPN provides a high level of data protection and anonymity online. Your internet traffic is encrypted twice, and your IP address is hidden behind two servers, making it nearly impossible to trace your online activity. Double VPN is the ideal solution for professionals and companies working with confidential information requiring a heightened level of protection.
VPN+Tor: Maximum Anonymity
Connecting to a VPN and then to the Tor network provides the maximum level of privacy that Tor can offer. This approach also helps hide your original IP address from Tor nodes, adding an extra layer of protection.
It is important to remember that using Double VPN or VPN+Tor may reduce internet connection speed, but this trade-off provides an additional level of security and privacy.
Why Do I Need a VPN?
The use of Virtual Private Networks (VPNs) has been on the rise in recent years. But why exactly do you need a VPN, and how can it ensure your security on public Wi-Fi networks? Let's explore a few key points.
Protection from Cybercriminals and Data Interception
In public Wi-Fi networks, such as those provided in cafes, airports, or hotels, your privacy and security can be at risk. Malicious actors can use methods like "packet sniffing" to monitor and intercept the data you transmit through unsecured Wi-Fi routers. A VPN creates an encrypted tunnel between your device and the VPN server, making your data inaccessible to hackers.
Anonymization of Online Activity
A VPN hides your real IP address, replacing it with the IP address of the VPN server. This allows you to use the Internet anonymously and securely. Your internet service provider and other third parties cannot see your traffic and cannot track your online activities.
Protection of Personal Information
A VPN prevents the theft and sale of your data, such as email accounts, banking details, and photos. When using a VPN, your data is routed from your device to the VPN server instead of directly to the internet provider, providing an additional layer of protection.
Bypassing Regional Restrictions
A VPN allows you to bypass internet resource blockages by connecting to a server through intermediaries.
Avoiding Targeted Advertising
A VPN can help you avoid intrusive targeted ads by hiding your real IP address. You decide what information about yourself to provide online.
Not Just Security, but Online Freedom and Privacy
Using a VPN is not only a matter of security but also a way to maintain your privacy online. When choosing a VPN service, pay attention to its reliability, speed, and privacy policy. Although a VPN is not an absolute safeguard against cyber threats, it significantly enhances your security in the online space.